Penetration Testing
Why Do You Need Pen Testing?

Services Available With Cyberleaf
This process provides internal or external scanning of endpoints and is offered as a single engagement, managed monthly/quarterly/bi-monthly service, or as a part of a penetration test package.
We simulate real-world attacks to provide a point-in-time assessment of vulnerabilities and threats to your network infrastructure. While many competitors usually perform a vulnerability scan and validate those findings against individual endpoints, we test your network wholistically. We combine techniques of penetration testing and red teaming to give you an attacker’s perspective of your entire network.
As a foundation for our web application assessment, our testing methodology utilizes the following: Open-Source Security Testing Methodology Manual (OSSTMM), Penetration Testing Execution Standard (PTES), Open Web Application Security Project (OWASP), just to name a few. This can include APIs and infrastructure as well.
Just like with web application testing, this process utilizes the following: Open-Source Security Testing Methodology Manual (OSSTMM), Penetration Testing Execution Standard (PTES), and Open Web Application Security Project (OWASP) methodologies to thoroughly assess the security of mobile applications.
Internet-aware devices span from everyday household appliances, thermostats, commercial Internet of Things (IoT) devices and systems, to automotive, healthcare, and mission critical Industrial Control Systems (ICS). We don’t limit ourselves to just the devices themselves, we consider the entire ecosystem of the target, covering areas such as communication channels and protocols, encryption and cryptography use, interfaces and APIs, firmware, hardware, and other critical areas.
It’s not a matter of if you will be a victim of social engineering, it’s when. We can help train your organization to understand, and detect human and electronic based social engineering attacks. Human-based attacks consist of impersonating a trusted individual to gain information or access to information and the client infrastructure. Electronic-based attacks consist of using complex phishing attacks crafted with specific organizational goals and rigor in mind. This service can be incorporated into a penetration test or can be utilized individually to help improve overall organizational training.
Want to know how prepared your organization’s defense, detection, and response capabilities are? Do they actually work as designed? Let us help you with developing a customized attack execution model to properly emulate the threats your organization faces. The simulation includes real-world adversarial behaviors and tactics, techniques, and procedures (TTPs), allowing you to measure your security program’s true effectiveness when faced with persistent and determined attackers.
Using methodologies previously described, we test your wireless capabilities to not only detect an attack, but what would happen if someone were to gain access to your wireless network. Is it properly segmented? Is there any protection from outside devices? Let us help you find out.
At the heart of every successful penetration test lies the seamless integration of people, process, and technology testing. Our team of skilled, certified professionals leverage their expertise to simulate real-world cyberattacks, ensuring your organization's security posture remains resilient. Our process begins by understanding your unique business environment, allowing us to tailor our approach to your specific needs. With rigorous testing methodologies, we meticulously identify vulnerabilities, test for exploits, and assess the effectiveness of your defense mechanisms.
Our team of seasoned professionals possess deep knowledge and understanding of regulatory frameworks, ensuring your organization remains compliant with industry standards and regulations. Our process begins by conducting a comprehensive analysis of your compliance requirements and tailoring our testing methodologies to address specific mandates. With rigorous assessments, we meticulously examine your systems, networks, and applications to identify any gaps or vulnerabilities that may pose compliance risks.
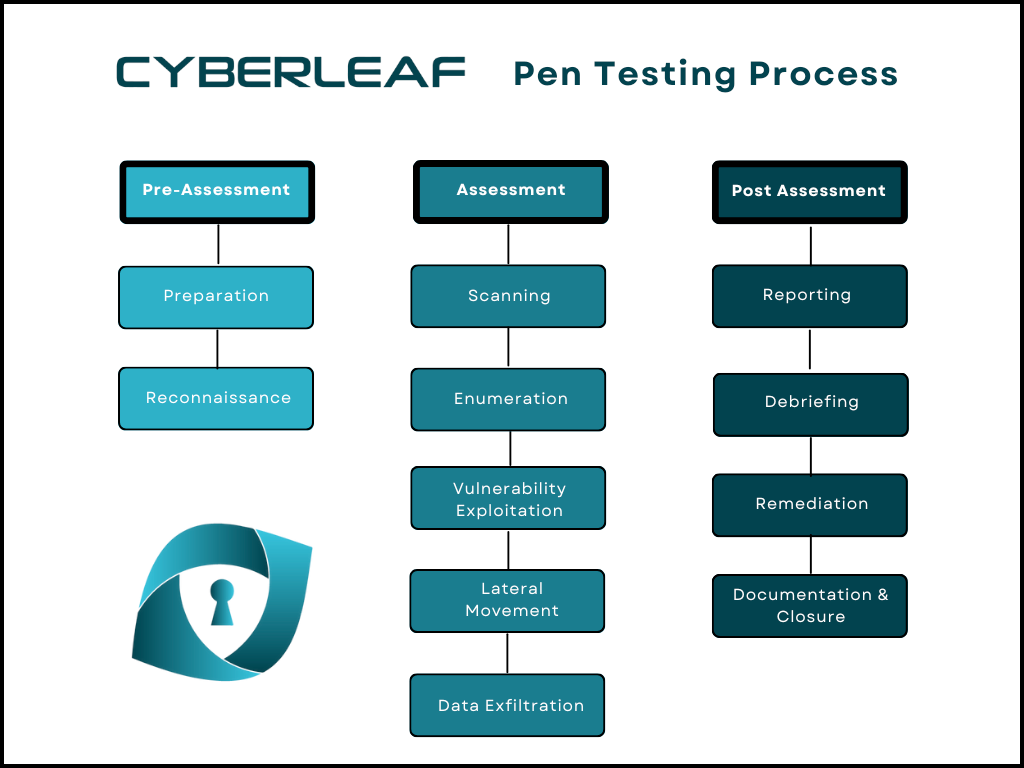
Why Choose Cyberleaf?
Along with 15+ years of combined experience,
our testers possess certifications in
OSCP, CRTO, CPTE & CDRE... just to name a few.









